To begin I would like to distinguish between identity theft and transactional credit fraud. Having your credit card or bank account number used to make a purchase is known as transactional credit fraud whereas using personal information (name, social security number, address, etc...) to establish new accounts in another's name is identity theft. These are both commonly lumped together as identity theft but they are different. The following information will help you defend against both.
For the rest of this article I will use the term "attacker" to indicate the bad guy that is going to steal someone's identity or commit credit fraud and I will use the term "victim" to indicate, well, the victim.
Both identity theft and transactional credit fraud originate when an attacker obtains sensitive information about a victim. This information can include (but is certainly not limited to) name, address, family member's names, credit card numbers, bank name, bank account number, bank account routing number, mother's maiden name, social security number (social insurance number for you Canadians), driver's license number, your pet's names, etc... You get the idea. There are many different ways that this information can be obtained and minimizing the potential of these ways is the focus of the rest of this article.
Online Activity:
First and foremost, keep your operating system and software up to date. Patch as soon as patches become available. Update your antivirus daily (most can be set up to do this automatically). Use a desktop firewall if you don't have a hardware firewall in place. Keep spyware off your machine. Failing to do any of this makes it easier for various types of scum-ware to make themselves at home on your machine and have free-reign on information you've stored there or process there.
References:
AVG - A free anti-virus
Windows Update
Ad Aware SE Personal - A free spyware removal tool
Online Accounts:
For those of us that have lots of online accounts, creating strong passwords that are different for every site is difficult but very important. Your bank spent a lot of time and effort creating a hashed web application login to protect your account information, you shouldn't destroy their efforts by using the same password for every stupid web forum and website that requires a login (most of which didn't spend two seconds thinking about security). There are tools available that allow you to store your passwords in a secure forum so you don't have to remember them all. The one I use is Just1Key. Information for all of my accounts is stored encrypted on their servers and I only have to remember one passphrase to access them all. Since I only have to remember the one passphrase I can make it very long and secure and I can change it frequently. Another product is Password Safe which was created by security expert Bruce Schneier. Password Safe is free, Just1key is not but it lets me access all of my account information from any computer with an internet connection. Here is a website that will help you generate strong random passwords that you can use for all of your accounts once you're comfortable with a password management solution.
A final thing to mention about securing online accounts is the use of secret questions. The correct way for a web application to use a secret question is to use it as a trigger to initiate a password reset sequence. It should not be accepted as an alternate to a password, it should only send an email to the user, at their registered email address, with information on how to reset their password. The problem is that many secret questions have answers which are easily discovered. Also, the keyspace for the questions is usually fairly small. What is your mother's maiden name? Think of the most common American surnames. What is your pet's name? Think of the most common pet names. What city were you born in? Think of the largest cities. The secret question should only be used to prevent abuse of the password reset feature of a web application. I routinely fill in garbage into these questions.
Shopping Online:
Merchants who accept credit cards are in violation of the payment card industry's (PCI) data security standard if they store credit card numbers in a readable form in their databases. There is little doubt that a lot of merchants do store credit card numbers unencrypted (think of all the news stories where credit card numbers were stolen). Because of this, do not use the "store my credit card number" feature of a web application if it is available. Use single-use account numbers if your credit card supports it. I can generate a single-use number that expires in two months and that has a spending limit just higher than my intended purchase.
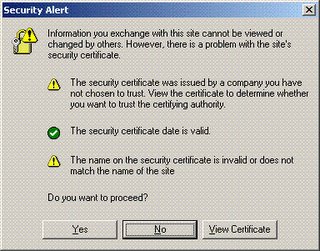
Whenever submitting personal information check your browser to see if the web traffic you're about to submit is encrypted. While browser dependent you will usually see a lock icon somewhere near the bottom of the browser. Additionally, the url will be prefixed with https (http over ssl). Seeing these two things let you know that the web site traffic is encrypted with SSL (so the casual snoop or packet sniffing cannot view your personal information). Beware, however, if these sites come with a certificate warning. A certificate warning means that something is wrong with the certificate that web site is issuing. This is a problem because it could indicate that someone is attempting to stage a man-in-the-middle attack. If your web traffic is going through a hackers machine and he tricks you into accepting his certificate, then all the traffic will be encrypted with a certificate that the attacker has the private key for. This would allow the attacker to decrypt any information encrypted with it. This is what the certificate warning looks like in Internet Explorer:
Shopping Offline:
A newer threat has surfaced whereby an attacker uses a cell phone with a camera to snap a photo of a credit card number when it is exposed. Because of this, when using a credit card in a public place take care to cover the number as much as possible. Cover the number with your finger when you take it out of your wallet or purse and hand it to the cashier. Don't set it on the counter or wave it around.
Don't sign the back of your credit card, instead write "SEE ID" on it. When cashiers check the signature on the back of the card you will have to provide your ID to them. In the event that your credit card is stolen or lost it will be more difficult for an attacker to use the card in a public setting (unless, of course, he also got your ID). I do this on all of my credit cards and while cashiers only ask for my ID about 30% of the time I don't mind giving it to them.
When using checks don't put your social security number or driver's license number on your checks. There is no reason for them to be on there and the few merchants that want your driver's license number can write it on the check themselves.
Personal Information:
Be suspicious of anyone asking for personal information over the phone, through email, in person, or on a form. This includes, your name (they're calling you, they should know that right), account numbers, routing numbers, PIN's, social security number, driver's license number, your birthday, your mother's maiden name or your dog's name. By default, if you don't initiate the communication I would refuse to give any of this information unless they can prove to you they're who they say they are. It would be a good idea to call the "organization" back if they say they need information. Most scams of this type are very physiological in nature so it takes the proper mindset to get used to avoiding these types of situations.
Get a decent paper shredder and shred anything with your name on it. Dumpster divers can discover a wealth of information about most people just from their junk mail. An attacker might learn enough to convince you they're who they say they are when they call asking for personal information.
Monitoring:
Obtain your credit report. The Fair and Accurate Credit Transactions Act of 2003 allows every American to obtain their credit report free once per year. You can check the report for mistakes or for accounts that you didn't open.
If you feel you have been a victim, close any accounts as soon as possible. Report the fraud to the three major credit bureaus Equifax, Experian, and TransUnion. You can file a complaint with the FTC using their online form.
References / More Information:
http://www.washingtonpost.com/wp-dyn/articles/A40992-2003Oct17.html
http://www.whitehouse.gov/news/releases/2003/12/20031204-3.html
http://www.usdoj.gov/criminal/fraud/idtheft.html
http://www.consumer.gov/idtheft/
1 comment:
Excellent article. Very informative and well written. Thanks.
Post a Comment